Best For | Secure identity management, SSO, and user authentication | Cloud-based threat protection, DNS security, and web filtering | Multi-factor authentication (MFA) and zero-trust security access |
In this blog post, let’s dive into my findings – eight compelling Perimeter 81 alternatives that have caught my attention.
Just as you’re seeking to fortify your data protection and enhance your digital infrastructure, I’ve been looking for options that can do just that.
With my research, you’ll be better equipped to make a decision that aligns with your cybersecurity needs.
In this fast-paced digital era, security isn’t a luxury – it’s a necessity. So, let’s explore these alternatives together and pave the way for a safer, more resilient business environment.
Your data deserves the best protection, and I’m here to help you find the right solution to make that happen.

A Brief Perimeter 81 Overview:
Building a secure network has never been easier with Perimeter 81.
Their innovative, cloud-based platform allows you to securely access your corporate networks regardless of location, giving you ultimate flexibility while providing enterprise-grade security.
Their easy-to-use web portal and mobile apps make it simple for any user to connect quickly in minutes.
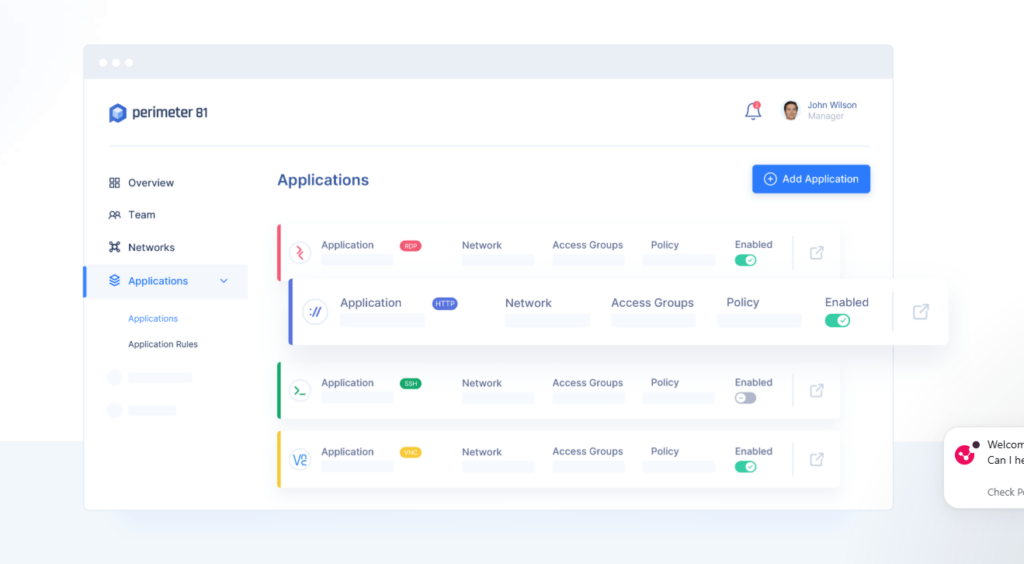
With Perimeter 81 alternatives, you can secure your business with the latest encryption protocols and best-in-class VPN technology.
Their Zero Trust Network security model provides a multi-layered approach to defending against external threats while allowing for granular network access control.
This means you have the peace of mind of knowing that only authorized users can access your corporate network and that their data is safe and secure.
Top 7 Perimeter 81 Alternatives 2026: Top Picks
1. Okta:
As one of the leading Perimeter 81 alternatives, Okta excels in identity and access management with its seamless Single Sign-On (SSO) that simplifies user authentication across thousands of cloud apps.
Okta uses the cloud to enable users to access applications from any device connected to the internet while maintaining strict security standards.
It relies on existing databases and identification systems and also 4,000+ programs.
Because Okta is built on an integrated system, businesses may swiftly deploy the services at a wide scale while keeping the total cost of ownership minimal.
Hundreds of companies, like Adobe, LinkedIn, Western Union, Allergan, and Chiquita, rely on Okta to help them manage quicker, generate more income, and remain protected.
Features:
- Single Sign On (SSO): Okta enables users to access all their cloud-based applications from one unified login. This eliminates the need to remember multiple logins and passwords, providing users with a simplified and secure way of accessing applications.
- Multi-Factor Authentication (MFA): Okta provides additional security by requiring more than just one authentication factor upon login. This might include physical tokens, biometric information, or questions related to personal details.
- User Lifecycle Management: Okta streamlines the entire user experience, from onboarding new users to changing existing roles or revoking access. This can be done in a centralized platform, saving your business time and resources.
Best For: Companies prioritizing identity-first security, Single Sign-On (SSO), and seamless user authentication.
2. Cisco Umbrella:
Cisco Umbrella provides cloud-based security whenever and wherever you need it.
As a Perimeter 81 alternative, it offers intelligent threat detection and real-time blocking of malicious activity, ideal for organizations needing resilient, cloud-based protection.
Umbrella is the quickest and most effective approach to safeguard your users anywhere in the world.
Features:
- DNS-Layer Security: Blocks threats at the earliest possible point, preventing malicious content from ever reaching your endpoints or network.
- Secure Web Gateway (SWG): Provides deeper inspection and filtering for all web traffic, allowing for granular control over user activity and application usage.
- Cloud-Delivered Firewall (CDFW): Offers firewall protection to enforce security policies for all internet-bound traffic, providing consistent security for all locations and remote users.
Best For: Businesses of all sizes wanting best-in-class threat intelligence and DNS-layer security to block threats before they reach the network.
3. Duo Security:
The Trusted Access technology from Duo Security provides protection, information, and services from hostile attackers and safety breaches. Our goal is to keep you safe while you are on the job.
Duo Security takes the burden out of protection so that you can concentrate on what matters most.
This Perimeter 81 alternative stands out for flexible user authentication methods and data loss prevention features
When your users interact with the applications you need them to access, we check their identification and equipment condition.
Features:
- Intuitive Multi-Factor Authentication: Famous for its easy-to-use push notifications, making secure login simple for all users on any device.
- Device Trust and Endpoint Visibility: Checks the security posture of devices (e.g., up-to-date OS, screen lock enabled) before allowing them to access applications.
- Secure Single Sign-On (SSO): Provides a centralized access portal for users to securely access their cloud applications after verifying their identity with Duo MFA.
Best For: Organizations seeking a simple, user-friendly way to implement multi-factor authentication and establish trust in users and devices.
4. BetterCloud:
BetterCloud is the foremost SaaS Management Platform (SMP) that helps IT workers focus, administer, and protect the modern workplace by expanding the stack of SaaS apps. It is a vital Perimeter 81 alternative for organizations seeking to streamline SaaS operations securely.
Many forward-thinking companies, including Zoom, Walmart, and Square, currently rely on BetterCloud to improve their SaaS rankings, thereby enhancing operations and maintenance efficiency.
By computerizing applications and user monitoring, and increasing power with centralized enforced security protocols, thanks to an expansive ecological system of SaaS implementations.
Features:
- SaaS Application Discovery: Scans your environment to reveal all SaaS applications being used, including shadow IT, so you can manage what you know.
- Automated Workflows: Automates complex IT processes like user onboarding and offboarding across multiple SaaS apps with zero-touch workflows.
- Centralized Policy Enforcement: Allows you to set and enforce security policies, such as data sharing rules and file permissions, across your entire SaaS stack.
Best For: IT teams needing to discover, manage, and secure their sprawling ecosystem of SaaS applications.
5. Citrix Workspace:
Citrix Workplace is a comprehensive digital workstation system that provides employees with secure access to the data, applications, and resources they need to perform their jobs.
Users pay for a service you provide and also use it from every location and on every device.
Citrix Workspace enables you to organize and handle the essential information that your users require in order to collaborate, make smarter decisions, and stay focused on their job.
Features:
- Unified Digital Workspace: Consolidates access to all apps (SaaS, web, virtual, mobile) and files in one interface, improving user experience.
- Built-in Secure Access: Provides ZTNA to private applications and adaptive authentication to ensure users and devices are trusted.
- Performance Optimization: Leverages the HDX protocol to deliver a high-performance experience for virtual apps and desktops, even on low-bandwidth connections.
Best For: Companies already invested in the Citrix ecosystem that want to provide a unified, secure digital workspace for their employees.
6. CyberArk Idaptive:

Adaptive Services is a great Perimeter 81 alternative that focuses on adaptive access with contextual security, offering strong Multi-Factor Authentication (MFA) and enterprise mobility management to protect against credential attacks.
Adaptive’s Next-Gen Access distinctively combines Single Single On (SSO), Adaptive Multi-Factor Authentication (MFA), and Enterprise Mobility Management (EMM).
User Behaviour Analytics (UBA) is an integrated system designed to protect against the primary point of attack in security breaches — compromised credentials.
Features:
- Risk-Adaptive MFA: Analyzes user behavior and contextual signals to apply the right level of authentication, reducing friction for low-risk sign-ins.
- Secure Web Sessions: Can record and isolate privileged sessions to sensitive systems, preventing malware from jumping from an endpoint to a critical server.
- Broad Identity Security: Offers a single platform to secure workforce, customer, and machine identities, providing a holistic approach to identity management.
Best For: Enterprises focused on securing identities, particularly privileged accounts, with risk-adaptive controls.
7. NetSkope:

Netskope is the industry leader in cloud security, assisting the world’s leading enterprises in leveraging cloud and digital technologies without compromising their security.
Customers benefit from 360-degree information and threat security with our Cloud XDTM technology, which targets and manages actions across any cloud storage service or website. This is what we refer to as “smart cloud security.” As a viable Perimeter 81 alternative, it ensures comprehensive visibility and control over cloud environments.
Features:
- Advanced Data Loss Prevention (DLP): Accurately identifies and protects sensitive data across thousands of cloud apps, whether the data is at rest or in motion.
- Granular Cloud and Web Control: Goes beyond simply allowing or blocking an app, enabling policies like “Allow viewing of files in personal Dropbox, but block uploads.”
- Unified SSE Platform: Provides ZTNA, SWG, and CASB from a single agent and management console, reducing complexity and improving security posture.
Best For: Large enterprises needing deep visibility and granular control over data moving across cloud applications and the web.
Why Consider Perimeter 81 Alternatives?
Choosing among Perimeter 81 alternatives depends on your organization’s unique needs—whether for more granular control, integration capabilities, pricing structures, or advanced security features like zero-trust access and multi-factor authentication. These alternatives offer a range of deployment options from cloud to hybrid architectures and varying scopes of network visibility and access control.
FAQs: Perimeter 81 Alternatives 2026
Are Perimeter 81 alternatives limited to cloud-based solutions?
No, alternatives range from cloud to on-premise and hybrid, providing options based on business control and management preferences.
Why would I consider Perimeter 81 alternatives at all?
Many teams like Perimeter 81 but explore alternatives for better identity integration, different pricing, on‑prem/hybrid needs, or deeper SaaS and data‑level controls than a pure network‑access solution offers.
Can Perimeter 81 alternatives integrate with existing security infrastructure?
Most alternatives support integration with popular identity providers, cloud services, and endpoint protection, but it’s crucial to verify compatibility upfront.
What features should I prioritize in Perimeter 81 alternatives?
Key features include ease of deployment, secure remote and zero-trust access, multi-factor authentication, cloud or hybrid deployment options, and robust threat detection.
Quick Links:
Conclusion: Perimeter 81 Alternatives 2026
In 2026, the best Perimeter 81 alternatives aren’t one‑size‑fits‑all: Okta and Duo shine for identity, Cisco Umbrella and Netskope for cloud and web security. NetMotion and Citrix for remote access and workspaces, and BetterCloud and CyberArk Idaptive for SaaS and identity governance.
Your ideal choice depends on whether you want to secure the network, the identity, the apps, or all three in different layers.



